Over two years ago, we launched our first hosted offering for Dolt. Since then, we have added features like the SQL workbench, support for Google Cloud and Single-sign on support with SAML. Up until now, our hosted offerings have all been database instances that we launch with publicly routable IPv4 addresses, through which customers connect to the instances. Hosted Dolt relies on TLS for endpoint authentication and confidentiality, and it relies on authentication and authorization of database accounts at the SQL layer to secure access to the database instance itself.
While this works well for some customers and some databases, other use cases need more control over the accessibility of the network endpoints for their database services. For a while now, we have been building the backend to support Hosted Dolt instances which are only accessible from a customer’s AWS VPC. We’re still putting the finishing touches on the feature, but we broadly know how it will work and what functionality it will offer. It uses the same network topology and security settings which use to run DoltHub on Hosted Dolt. In this blog post, we’ll walk through what Hosted Dolt Private Deployments are, how they will work, and ways in which they will be different from public ones.
Hosted Dolt Private Deployments#
A Hosted Dolt Private Deployment will operate similarly to existing Hosted Dolt deployments. It will run on cloud instances that are managed by the Hosted Dolt control plane, and database maintenance and administration will be the responsibility of the Hosted Dolt team. The instances will be launched into private VPCs owned and operated by Hosted Dolt. Instead of exposing the resulting instances to the public internet and publishing DNS entries to allow customers to connect to their database endpoints, Private Deployments will use AWS PrivateLink. Customers will be able to create network endpoints within their own VPCs that allow access to the deployed Hosted database instances.
This is the network diagram for a deployed public instance has customer instances launched into a VPC with an internet gateway and direct access to every replica in database cluster:
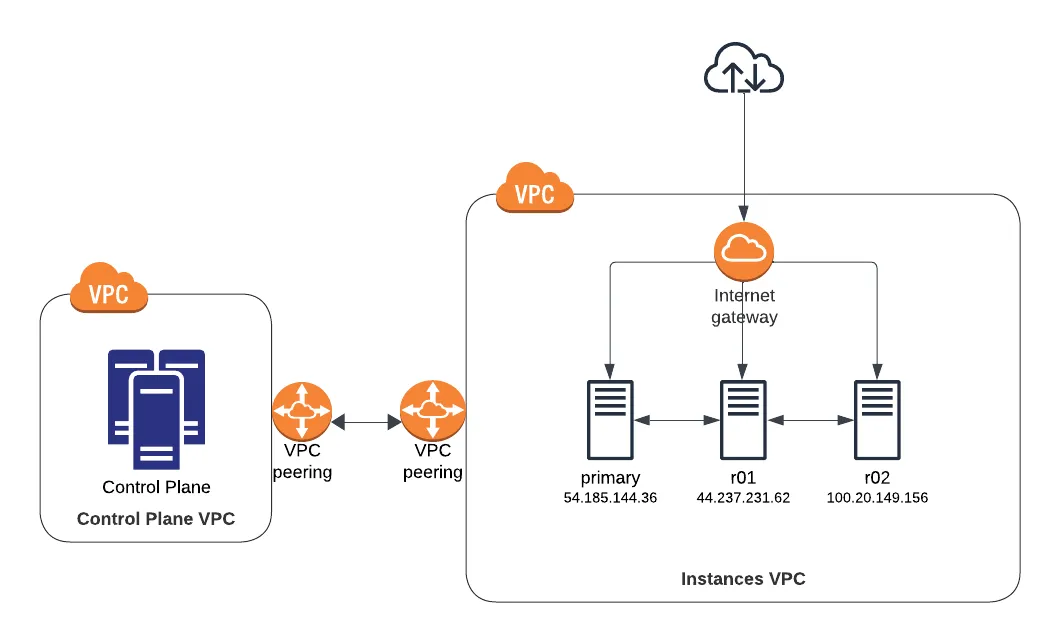
The hosted control plane manages DNS names for the database endpoints, and needs to update them in the case of replicas being added or removed from a cluster or the primary database of a cluster changing.
AWS PrivateLink works slightly differently. VPC endpoint services published in one VPC allow for the creation of one or more VPC endpoints in one or more client VPCs. Those endpoints then become the network devices through which clients within those VPCs can access the services in the publishing VPC. VPC endpoint services always sit in front of AWS Elastic Load Balancers. And to connect to one, infrastructure needs to be created in the consuming VPC. This motivates a slightly different topology and naming convention than for Hosted Public Instances. Overall, the network diagram ends up looking like this:
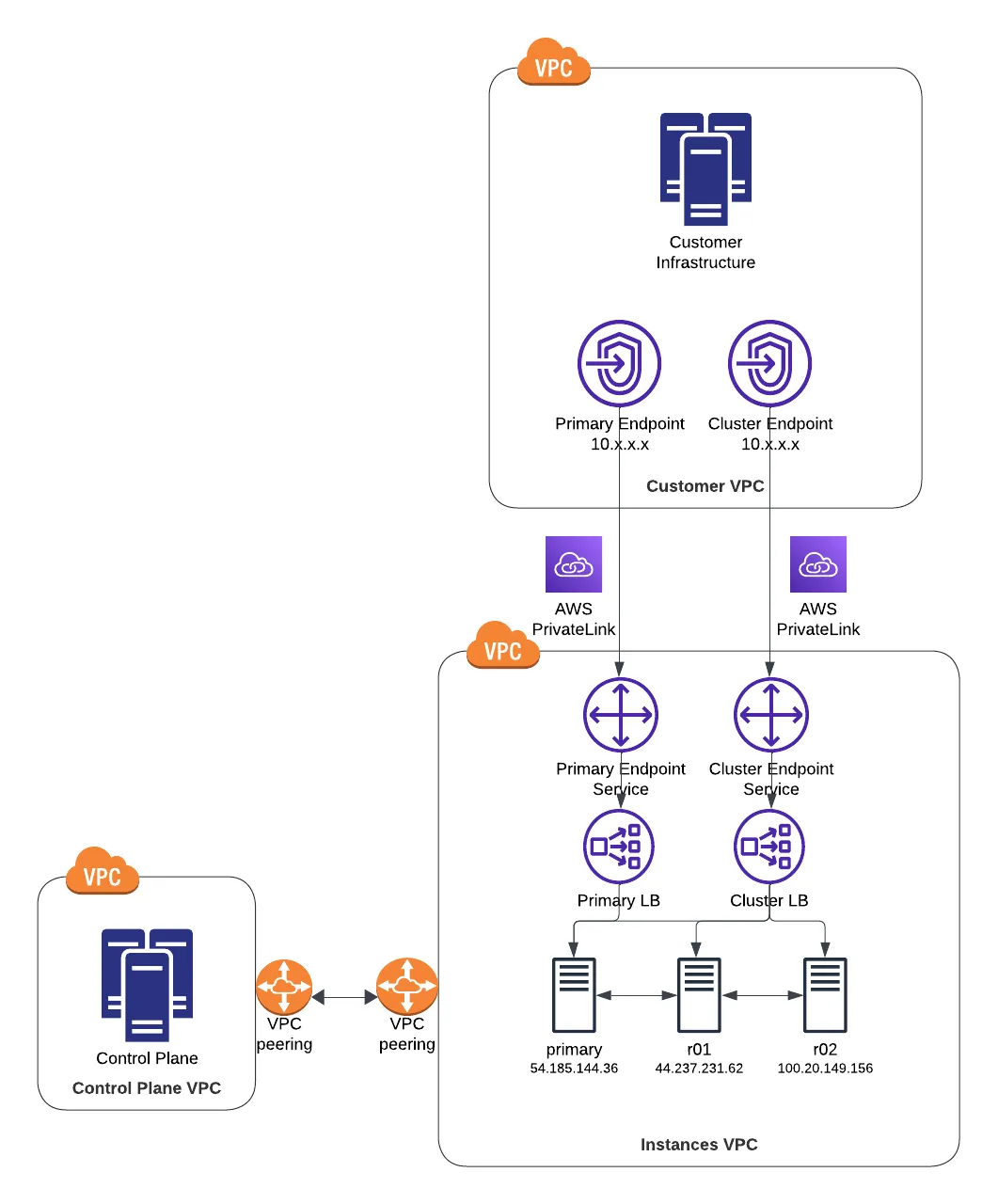
Expected Changes#
You can expect the following changes and tradeoffs when launching Hosted Dolt Private Instances.
-
New clusters will take a bit more time to provision. More infrastructure needs to be provisioned and initialized, including elastic load balancers, as well as DNS verification on the created VPC endpoint services needing to be completed. Typically provisioning time can be up to 20 minutes, compared to less than 5 for public deployments.
-
You will connect to your primary instance at
owner-deployment-name-primary.dbs.hosted.doltdb.comand there will be a single DNS endpoint for all hosts in the cluster atowner-deployment-name-cluster.dbs.hosted.doltdb.com. When the cluster topology changes, only the targets behind the load balancers need to change, and so adding or removing replicas from a cluster does not change the network endpoints to which your applications need to connect. -
After creating a new cluster, you will need to create VPC endpoints within your own VPCs to access the endpoint services that correspond to your new deployment. You will need to provide a list of AWS account IDs which are allowed to access the cluster. After that you can create the VPC endpoints using the service names which will appear for your cluster on the Hosted Dolt website.
-
When a cluster is deleted, its corresponding Endpoint Services are deleted as well. You will need to delete the VPC Endpoints which were created to access the cluster from your own VPCs.
-
Private Deployments will cost slightly more per hour than public deployments.
-
And, of course, the endpoints for connecting to Private Deployments are only available from VPCs which have connected to the VPC endpoint services associated with the private deployment. They do not have public IP addresses and are not accessible from the internet.
Overall, lots of things do not change:
-
Hosted Dolt still runs and manages all hardware and OS resources associated with deployment.
-
Logs and monitoring for the instances are accessible from the Hosted dashboard as expected.
-
Backups from public instances are restorable to new private instances, and vice versa.
-
Using the endpoints for a Hosted Private Deployment as a Dolt remote endpoint works as expected. The VPC endpoints expose the
doltremoteapiservices which Dolt needs to clone, pull and push to the Hosted Dolt instance. -
WebPKI certificates for the endpoints associated with the deployment are still available and certificate verification from clients works as expected.
-
Trial instances will be available for Private Deployments.
When Hosted Private Deployments first launch, the SQL workbench will not work with them. We hope to make the SQL workbench work with Private Deployments shortly after launch.
Conclusion#
With Private Deployments, Hosted Dolt will be appropriate for even more use cases. Private Deployments are appropriate for anyone who wants to keep their database deployment off the public internet, and is willing to do some configuration within their VPCs in AWS in order to do so. If you have a use case or feature request for Private Deployments, please don’t hesitate to contact us or drop by our discord to discuss.